Linux Open Port - A Complete Guide

A port is known as a communication endpoint in an operating system. An open ports in Linux can be opened or closed to data or determined process network services. TCP and UDP ports are typically used to identify specific network services that are designated to them. Users can change it manually by configuring the service using a separate port. You can also use open ports in Linux by default in general.
Port numbers range from 0 to 1023, the first 1024 ports, are commonly known port numbers reserved for widely used services. It includes port 22, which is SSH; port 80, which is HTTP; and port 443, which is HTTPS. Port numbers that are above 1024 are Ephemeral Ports. Following are the detailed ports:
-
1024 - 49151 port numbers are named as registered/user ports
-
49152 - 65535 port numbers are named dynamic or private ports
Understanding a Port and Reason to Open it

Open ports in Linux are like a gateway that leads the user to a particular room on a Linux system. Everything a user does on the internet, or it might be a series of open ports, uses a specific port.
For instance, if you plan to run your web server, you must use open ports in Linux to connect. The same procedure applies to running your web, FTP server or mail. Ports are network connections across all network-connected devices.
How To Open a Port on Linux
Open ports in Linux involve the firewall configuration mechanism to allow network traffic via specific ports. See the basic measures using the UFW (Uncomplicated Firewall) tool, which is generally used on Debian-based systems. If you are using a different distribution, the steps might vary.
Using UFW (Uncomplicated Firewall)
Users should be cautious when opening ports, particularly on a public-facing web server. Only open the ports that are essential for your applications. You can also consider using strict firewall rules and other security measures to guard your system.
Check UFW Status:
First, confirm that UFW is installed and review its status.
sudo apt-get update sudo apt-get install ufw sudo ufw status
Develop a Specific Port: You can utilize the allow command by the number of port and the protocol to develop a specified port (usually TCP ports or UDP ports). For instance, to open port 80 for HTTP traffic:
sudo ufw allow 80/tcp
If you want to open a range of ports:
sudo ufw allow 3000:4000/tcp
Allow Specific Application: You can also allow traffic for a specific application. For example, to allow SSH traffic:
sudo ufw allow OpenSSH
Check the Updated Rules
Verify the rules to ensure the changes have been applied.
sudo ufw status
Reload UFW
After making changes, you might need to reload UFW for the new rules to take effect.
sudo ufw reload
Enable UFW
If UFW is not already enabled, you can help it using:
sudo ufw enable
Confirm the action by typing 'y'.
Using Firewall-cmd (For Systems with firewalld)
If your Linux system uses Firewalld instead of UFW, you can use the following steps:
Check Firewall-cmd Status:
sudo firewall-cmd --state
Open a Port:
sudo firewall-cmd --add-port=80/tcp --permanent
Reload Firewall-cmd:
sudo firewall-cmd --reload
Check Open Ports in Linux:
sudo firewall-cmd --list-ports
Listing Open Ports in Linux

Before unlocking a port number on a Linux system, you must review if the required port has already been opened. The most manageable way to learn about an open port in Linux is to use a command line of the netstat command to grep command.
netstat -na | grep :[port-number]
The overhead command line suggests the grep to search for a special port number in the port list delivered by netstat command. For example, to inspect if port 8080 is obtainable on the system, enter the following command:
netstat -na | grep :8080
If the port is closed, the command produces no result.

Use the subsequent netstat command to portray an index of listening port:
netstat -lntu
The -l alternative search for the listening ports
-n provides numerical port values
-t and -u stand for TCP port and UDP port, respectively.
Opening a Port in a Linux
The right process to open a port in Linux depends on the firewall you are using and the Linux distribution. Following are the common scenarios for which the steps are recommended:
-
Firewall on RHEL-based distribution and CentOS distribution
-
UFW firewall on Ubuntu-based distribution
-
The iptables utility without firewall and UFW for the system
Ubuntu and UFW Based Systems

UFW, or Uncomplete Firewall for Ubuntu, allows you to open a port with a single command. The command line is:
sudo ufw allow [port-number]
when you add IPv6 and IPv4 rules, the output is confirmed. Alternatively, you can see an open port in Linux used by a specified service without entering the port number. Command will be
sudo ufw allow [service-name]
To see if the UFW is active on your system, you can check by entering the following command:
sudo ufw enable
Systems with Firewalld
Fedora, firewalls tool and other relevant distributions allow the user to control port access on their Linux. To open a specific port, utilize the subsequent command:
sudo firewall-cmd --zone=public --add-port=[port-number]/[protocol] --permanent
The --permanent ensures the persistence of rules after the system reboot. However, the --zone=public argument is useful for multi-zone system configurations. Firewalld assign all interfaces to the public zone by default.
Without UFW or Firewalld Linux Distribution

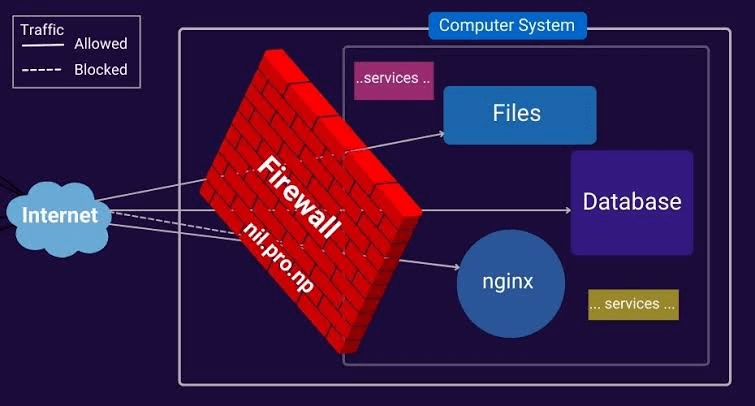
While nestling a full-fledged firewall is suggested to support system security, some Linux distributions use the legacy iptables solution. To filter IP packets using the Linux kernel firewall, iptables utility is allowed by configuring rules. To initiate an iptables utility rule for open port, use the following command:
sudo iptables -A INPUT -p [protocol] --dport [port] -j ACCEPT
This command will create IPv4 rule.
For IPv6 rule, use the ip5tables command like:
sudo ip6tables -A INPUT -p [protocol] --dport [port] -j ACCEPT
The port number specifies the --dport option. However, the -p flag define the protocol (udp ports or TCP ports). To produce and IPv4 rule for TCP ports 8080, put in the following command:
sudo iptables -A INPUT -p tcp --dport 8080 -j ACCEPT
Debian-Based Systems iptables Rules
The rules are developed using iptables that do not continue after reboots. Heed the steps below to fix iptables rules after a reboot on Debian-based systems:
Save the IPv4 rules you initiated by entering the following command:
iptables-save > /etc/iptables/rules.v4
To store any IPv6 rules in a separate file, enter the command mentioned below:
ip6tables-save > /etc/iptables/rules.v6
For installation of the iptables-persistent package, use the command below:
sudo apt install iptables-persistent
It will reload the contents of rules.v4 automatically with the rules.v6 files when the system is restarted or rebooted.
Iptables Rules Persist on RHEL Systems
Iptables configuration is stored on a different location by RHEL-based systems.
To hold the IPv4 rules or IPv6 rules, tag the following command:
iptables-save > /etc/sysconfig/iptables
Or,
ip6tables-save > /etc/sysconfig/ip6tables
To review if the iptables-services package is lodged, use the following command
sudo dnf install iptables-services
Enter the command to initiate or activate the device
sudo systemctl start iptables
Allow the service by the command below:
sudo systemctl enable iptables
To protect the iptables rule, use the command:
sudo service iptables save
To implement the rule, continue the service by documenting the command as:
sudo systemctl restart iptables
Testing Open Ports in Linux
By using any of the way to open a port in Linux, confirm that the process is finished successfully. To check the open ports on a system, follow the method below.
View the listening ports with the netstat command:
netstat -lntu
To list the open socket, use ss command as:
ss =lntu
By using the nmap command, you can test the port by specifying its number. For example use the nmap command:
nmap localhost -p 8080
Use netcat utility or netcat command to test the port. By using netcat command, you can test an open ports. This tool also features nc command.
Use echo command to pipe output to netcat command and determine the port to listen
echo "Testing port 8080"| nc -l -p 8080
Leave the command in running process and open a new terminal window to query the local socket. use the command as:
telnet localhost 8080
Conclusion
Understanding incoming connections, conducting a beginning port test, and scanning open ports are fundamental aspects of computer networking. Whether configuring a web server, managing assistance, or evaluating the state of active connections, the facts of TCP and UDP ports is essential. The dissimilarity between an open TCP port and a closed one and identifying the importance of utilizing the same port for parameter passing underscores the difficulties of providing effective and secure transmission within a network. The ability to scan open ports facilitates comprehensive monitoring, enabling network administrators to maintain the integrity and functionality of their systems while addressing potential vulnerabilities.
Frequently Asked Questions
What are TCP ports in Linux, and how do I open TCP ports?
TCP (Transmission Control Protocol) ports are communication endpoints. You can open them in Linux using firewall management tools like UFW or firewalld.
How can I identify listening ports on a Linux?
Use the ss command to list listening ports on a Linux. For example: ss -lntu displays TCP and UDP listening ports.
What are UDP ports, and how do I open them on a Linux system ports?
UDP ports (User Datagram Protocol) are another type of communication endpoint. Open them using firewall tools like UFW or firewalld in a manner similar to TCP.
How can I monitor open ports in Linux using the lsof command?
Use the lsof command to list open ports and associated processes on a Linux system. For example, lsof -i in lsof command provides details on open connections.
How do I check for open ports on a Linux from the command?
Utilize command line utility like netstat command or ss command to check for open ports. For instance, ss -a lists all open ports, including listening port and established connections.
What is the significance of monitoring listening sockets on a Linux server?
Monitoring listening sockets using tools like ss or lsof helps identify services actively waiting for connections, enhancing network security.
How do I open specific TCP port and UDP network ports on a Linux system?
Open TCP network ports and UDP ports by specifying the protocol and port number using firewall management tools, such as UFW or firewalld.
What command can I use to identify listening ports on a Linux server in real-time?
The ss command with the -r option provides real-time monitoring of network connections, including listening ports, on a Linux operating system or Linux server.
How can I use the ss command to display open ports connections on a Linux server?
The ss command, when used with the -a option, displays both listening and established connections, offering a comprehensive view of network activity.
What is the recommended way for monitoring network connections on a Linux server?
To monitor network connections efficiently, consider using a combination of tools like ss, lsof, and firewall management utilities to ensure a robust approach to network security.










 (1).png)