Configuring a secure SSH-based connection to your VPS server
Introduction
SSH is a go-to method of connecting to remote servers, VPS or not. It is handy, multiplatform ( there are ssh clients even for mobile devices ), allows you to control the machine almost as if you were sitting in front of it and has a lot of useful features. However in the modern IT world a huge emphasis is put on security, so i am going to share a few details on how to secure your ssh access. You will create a pair of keys: private and public. Private is your secure key, that you should protect, keep safe and not share with anyone. It is used to identify you as a unique user. Public is a key, that can be distributed to remote server or service. It is a public part of the created key-pair, and identifies itself with a private key. So when you access a server or service with a private key, it's compared to public key, stored on that remote machine and if they match, you are allowed to access.
Prerequisites
You'll need:
1) CentOS 7.4 VPS server
2) Basic knowledge how to edit files in Linux systems
3) Linux or Windows host machine, from which you access the VPS server.
Generating a ssh key pair on your host machines
If your system, from which you access VPS, is Linux ( Fedora 25 system was used, as a typical home/workplace Linux system):
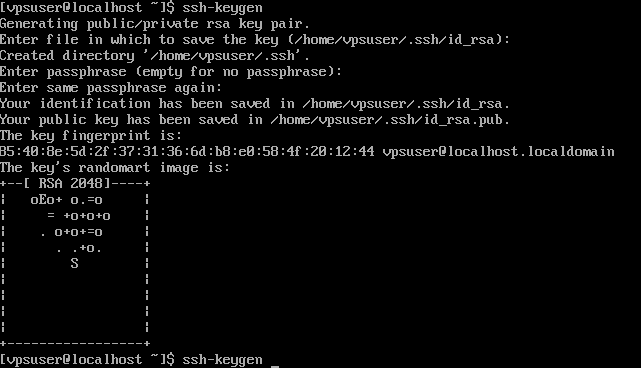
1) run ssh-keygen and follow on-screen instructions
ssh-keygen
You will be prompted to enter a key storage location ( you may leave it as is ). ssh-keygen will also request you to enter the password to protect the key. While key can be left passwordless, as it is sometimes useful for specific configurations ( automated systems, without a user input ) it is recommended to protect your key with a password, so even if key pair is compromised, your key solely will not allow attacker to reach VPS server.
Remember the password. If you forget it, there is no way to restore access to your key.
2) Backup your keys on a secure, safe storage
3) run
cat /home/vpsuser/.ssh/id_rsa.pub ( replace path with the one, you have actually used ) and copy the key.

4) You need to put a copied key as a new string into
`/root/.ssh/authorized_keys`
on your VPS server. It should look like this
 Notice that each key starts as a separate string.
5) To connect from linux machine to your VPS server through ssh, you just need to run
Notice that each key starts as a separate string.
5) To connect from linux machine to your VPS server through ssh, you just need to run
ssh -i /home/vpsuser/.ssh/id_rsa.pub root@<your server ip>

If your system, from which you access VPS, is Windows ( Windows 10 was used, as a typical home/workplace Windows system):
1) Run puttygen tool, that comes out of the box with a putty installation.
If you system lacks puttygen, or you use a portable version of putty binary, download 32bit or 64 bit binary from
https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html[1]
 2) Press "generate" and it will ask you to move mouse on the empty area to generate random data, and will provide you an ssh key pair.
2) Press "generate" and it will ask you to move mouse on the empty area to generate random data, and will provide you an ssh key pair.
 2.1) Enter password to "Key passphraze" and confirmation fields. Remember the password.
2.2) Copy the contents of the "public key for pasting into Openssh authorized_keys file:"
2.3) Save public and private key to a secure, safe storage
2.1) Enter password to "Key passphraze" and confirmation fields. Remember the password.
2.2) Copy the contents of the "public key for pasting into Openssh authorized_keys file:"
2.3) Save public and private key to a secure, safe storage
3) Copy's the contents of the "public key for pasting into Openssh authorized_keys file:" windows in puttygen 4) Go back to your VPS server. We need to add the public part of the key pair, we have just created to the list of authorized keys. Put a copied key as a new string into
/root/.ssh/authorized_keys
On your VPS server. It should look like this
 Notice that each key starts as a separate string.
5) Test connection to your VPS server
5.1) Open putty and go to Connection - SSH - Auth in the left panel.
5.2) Open you private key file by pressing Browse near the Private key for authentication field
Notice that each key starts as a separate string.
5) Test connection to your VPS server
5.1) Open putty and go to Connection - SSH - Auth in the left panel.
5.2) Open you private key file by pressing Browse near the Private key for authentication field
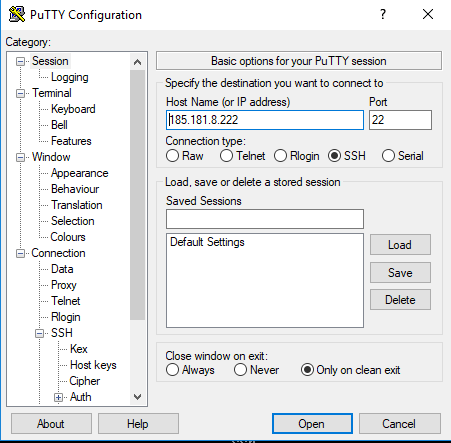
 5.3) Go back to Session in the left panel of putty, enter your server hostname or ip with a login name ( optional, as putty will prompt for it anyway ) and press Open.
5.3) Go back to Session in the left panel of putty, enter your server hostname or ip with a login name ( optional, as putty will prompt for it anyway ) and press Open.
 5.4) Putty will prompt for key password at it's screen, and if entered correctly, forward you to your VPS server console
5.4) Putty will prompt for key password at it's screen, and if entered correctly, forward you to your VPS server console

Securing your SSH server
Now you can safely login to your VPS server from both Linux and Windows machine. At this moment you should disable access with password to your machine, so all bruteforce attempts are useless. Your system will simply not accept any incoming ssh connection without an authorized ssh key. Open on your VPS server
/etc/sshd/sshd_config
and change PasswordAuthentication yes string to PasswordAuthentication no
restart sshd daemon
systemctl restart sshd
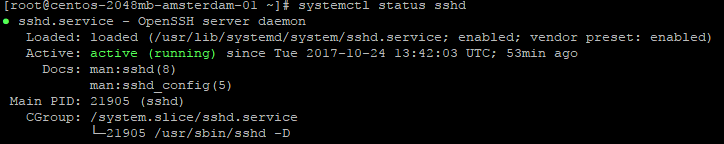
and check that it has no problems
systemstl status sshd
Conclusion
Securing your ssh connection with ssh key pair, and forbidding login with a password is considered a basic security measure. It protects your server from a lot of attacks, that are based on bruteforce and alphabetical password search. Always protect your VPS server at least with basic measures so you can sleep better :)
[1]: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html






