Comprehending Iptables List: A Guide to Understanding All the Iptables Rules

One of the most precious commodities in today's technological world is network security and supervised network traffic management. Most Linux systems have strong encryption codes and firewalls for optimized protection from malware. Among these firewalls are the iptables firewall rules, which provide security to any Linux server and effectively disable any threats.
What are Iptables?
Simply put, the iptable is a distinct form of firewall specifically designed for Linux systems. Having a good understanding of iptables is important for all users who want to start using Linux systems casually.
This utility is critical for packet filtering, managing configuration files, and regulating general network traffic. The basics of learning about iptables include learning about their rules. These rule specifications lay the framework for the working and functionality of iptables.
What are Iptables Rules?
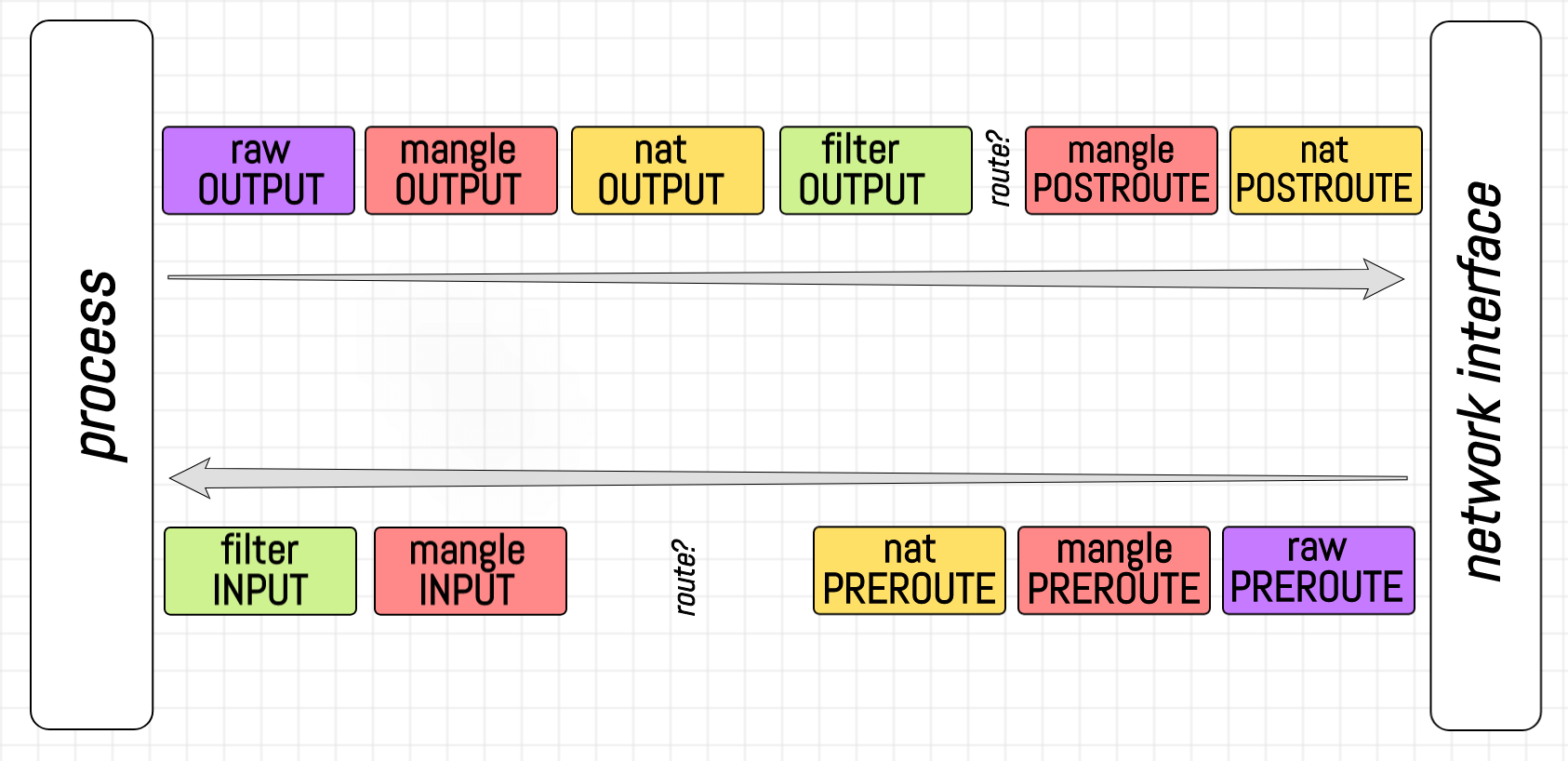
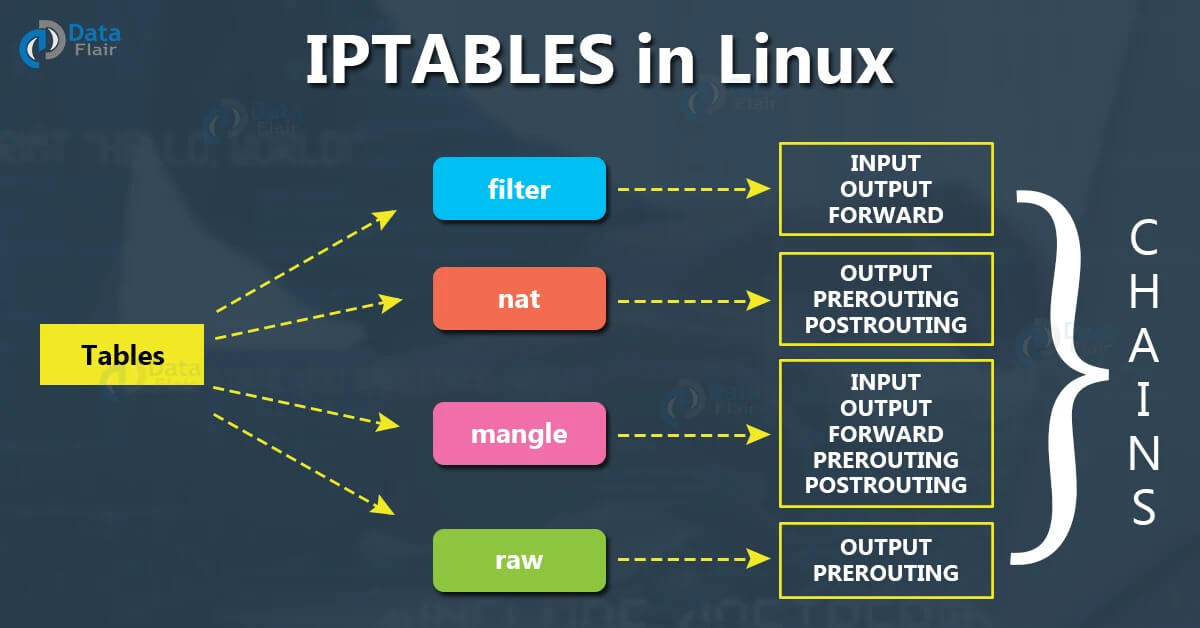
Iptables rules are existing rules that dictate the smooth working of a Linux server by handling incoming network traffic. These rules are organized into chains.
These chains represent a set of conditions and actions. These chains have a default policy that maintains the security of our Linux server.
Each iptable rule begins with a set of criteria known as match criteria. After the match criteria determines which action must be performed, the system implements the specified action. Some of the common actions given by the match criteria are:
-
Accept (allowing access to the packet)
-
Drop (discarding the packet without a response)
-
Reject (discarding the packet with a response)
Rule Example
A rule may be applied to block a specific IP address. If the action is specified by the match criteria, it will be written as:
iptables -A INPUT -s 129.826.9.4 -j DROP
This command drops invalid incoming packets from an IP address blocked by the user.
List of Iptables Command
By laying out active rules for iptables, we can focus individually on each command while following the table format. The following active iptables rules are given as:
Listing Rules
To display the current rules in the iptables firewall, the code is given as:
iptables -L
In the iptables rules configuration files, the 'listing rules' command is the most common form of iptables command. All the rules in the Linux system are an extension of this particular rule.
Listing Rules with Details
When it comes to listing iptables rules with extra information, additional components are added to the general iptable command:
iptables -L -v
Sometimes the iptables rules target prot opt source as part of their iptables commands. This is done to gain access to additional details about the iptables rules. The same is done when users list rules.
Blocking an IP Address
As mentioned above, the iptables rule applied to block undesired IP addresses is stated as:
iptables -A INPUT -s 129.826.9.4 -j DROP
The greatest feature of the NAT table is its ability to customize the type of packets that can enter the system. If the user does not find incoming packets appropriate, the user drops invalid packets and can also reset packet counts. This can also help with blocking SSH traffic.
Logging Rules
To log the packets into the system properly, the iptables command installed is written as:
iptables -A INPUT -p tcp --dport 76 -j LOG --log-prefix "HTTP Traffic: "
This rule clearly shows the prot opt source destination for the iptables command with the protocol, options, source, and destination stated in the command. The user should target prot opt source to ensure accuracy and details.
The interpretation for the above rule of the prot opt source destination is given as:
ACCEPT tcp -- 129.826.9.4 0.0.0.0/0
This particular rule is very important in understanding the background details of the rules. In this example, the tcp (transfer control protocol) is used alongside the source IP address and destination.
Saving Rules
All the changes made previously to the different types of rules in their respective chains would become null and void if the changes would not be saved in the system. For this purpose, the saving iptables rules are used:
iptables-save > iptables-rules
After writing this command, all the changes made to the rules are saved and there is no hazard of the data being lost. All users should always remember to save changes before moving on to the next operation.
Evaluation of Iptables Rules by Specification
Rule specification becomes very important when a user wants to limit scope and save time. These rules also help with applying functionality to a specific chain without affecting the other chains. For the listing of specific chain rules, the general command used is written as:
iptables -L INPUT
This input rule is a part of the input chain that deals with entering the rule into the system to output the desired results.
Delete Rules
To delete a specific rule from its chain, the specific chain and rule number are identified:
iptables -D INPUT 9
The 'delete rules' is a specific rule that deletes a rule from the given chain in iptables. Deleting rules from the wrong chain can lead to some disastrous outcomes. This is why it is always advised to be very careful whenever writing code for iptables.
Flush Rules
To remove all rules from their specific chains, the following command is used for flush chains:
iptables -F
Unlike the delete rules, the flush chains follow the firewall settings of resetting chains to default chains. These default chains end up in an unformatted state, unlike the non-default chains which are formatted.
Removing Rules
In all the iptables rules by specification, this is the only rule similar in nature to the delete rules but differs in the sense that this rule eliminates a rule from its specific chain.
iptables -F INPUT
This command removes all rules in the INPUT chain but doesn't remove the built-in chains themselves or their default policy.
Evaluation of Iptables by Chain's Rules
All the rules that are a part of the iptables rule can also be applied to the chains as a whole without using rule specification for all the active rules since being specific is not the answer all the time.
Listing Rule's Line Number
When the user wants to view rules in a chain with its respective line number, the command is written as:
iptables -L --lines-numbers
For the purpose of making referencing easier, the user can view the chain name with its line number. These list rules make the organization smoother and help improve the performance of the system.
Displaying Rules in Tabular Form
The general rule for displaying rules in the form of a table is the same when applied to the input chain as a whole. The following command is written as:
iptables -t filter -L
These list rules help with packet filtering. The packet counts also allow the process for the user to easily arrange packets in the system to increase readability.
Setting Time-based Rules
The '--time' option enables the user to apply rules based on specified time criteria. The command is written in the system as:
INPUT -p tcp --dport 64 -m time --weekend Saturday, Sunday -- timestart 20:00 -- timestop 23:00 -j ACCEPT
According to the command written above, the network will allow the flow of HTTP traffic in between a specific time on the weekends. Besides the specified time, the traffic will be restricted access.
Setting Default Policies
Our iptables command allows the user to set the default policy for a chain by establishing a default action for packets. The chain output (policy accept) is shown when the given command is written:
iptables -P FORWARD ACCEPT
This command will perform the same function as not accepting the iptables packet if it does not meet specified criteria.
Conclusion
Handling iptables may take quite some time and you must be skilled to manage it, however; one ought to do so without fail. Our Linux system only provides THE best command and prompt system to all our users. It also provides appropriate guidance and an interface that makes Linux easier for beginners.
Learning the configuration of iptables not only polishes the work of a professional programmer but also helps in maintaining a secure network for your server.
With our out-of-band console, users can use dedicated Linux servers with optimal performance and affordable offers!
Frequently Asked Questions
How to list all Iptables?
When it comes to the management of the Linux system, flushing and listing are two of the most common firewall rules. The implementation of listing firewall rules is given below:
The basic command for listing the iptables rules across all chains is written in the standard format:
iptables -L
For more advanced conditions, like listing all rules with line numbers to reference specific rules, the command is modified:
iptables -L --line-numbers
The general command for listing the iptables rules can have multiple variations depending on what the user wants. The user can replace 'INPUT' with the name of the chain they want to inspect or modify:
iptables -L INPUT
How do you flush iptables rules?
The flush iptables rules are necessary for all resetting tasks in the Linux servers. The general command for flushing the iptables rules across all chains is written in the standard format:
iptables -F
Similar to the list iptables rules, the user can replace 'INPUT' with the name of the chain they want to flush:
iptables -F INPUT
To delete all user-defined chains in the system, the user can employ the tactic given below. However, it is advised to use this command with caution since this command can also remove custom-built user chains.
iptables -X
How do you delete a rule that already has a functionality?
The general 'iptables -D' can be used on its own to delete a rule that already has a functionality. But you can use the sudo privileges to enhance your code by employing the following method to delete rules:
iptables -D <chain_name> <rule_specification>
The line given above is the general syntax of how to use sudo iptables with the help of a rule position to delete an already existing rule, thus proving that the question shows research effort.
Consider an example of a chain with a target to accept the incoming TCP traffic on port 2o from the IP address 129.826.9.4. The correct way of removing this rule would involve deleting the rule in the INPUT chain.
iptables -D INPUT -s 129.826.9.4 -p tcp --dport 20 -j ACCEPT
How to display rules in table?
The following command is used to display the iptable rules in a tabular form:
iptables -t filter -L
All the rules in iptables can be displayed using this iptables command. The best thing about this command is that it displays the rules without needing its prot opt source destination IP address.







 (1).png)




.webp)